Organisations of all sizes struggle to identify where to start their GDPR journey, but the process is even more challenging if your company needs to implement other information assurance schemes such as Cyber Essentials. In this article, we will discuss how GDPR and Cyber Essentials relate, and how to use an existing Cyber Standard to kickstart your GDPR journey.
What is GDPR?
Fundamentally, GDPR readiness is about identifying Privacy and Security risks and ensuring you have robust processes in place to enable data subjects to enact their rights.
The GDPR (General Data Protection Regulation) is a Europe-wide regulation (does not require implementation at the national government level, as opposed to a directive which does) that attempts to lay the foundations for two core areas in relation to the processing of personal information:
- Data Protection – ISO 27001, IASME and, to a lesser degree, Cyber Essentials
- Data Privacy – this focuses on a number of areas including Principles and individuals’ rights (Article 5, Article 13 to Article 22)
Data protection risk and the four T’s method
Data protection requirements are generally well understood. Take a risk-based approach and use one of the four T’s to manage the underlying dangers. For those of you unfamiliar with this approach, there are essentially only four actions you can take when risk has been identified:
- Treat – implement control(s) that will reduce either the likelihood or impact of the risk occurring
- Terminate – change your business processes to remove this risk from your organisation
- Transfer – this action typically takes the form of an insurance policy
- Tolerate – this is used where you have reviewed the other options and decide to take your chances that the risk will never occur.
Data protection requirements have been adopted by many organisations, either formally or informally. The more challenging area is around that of Data Privacy. In my opinion, several GDPR Articles are unclear and may encourage implementers to over- or under-comply. Data Protection is a new and challenging concept for many organisations.
The GDPR leaves the onus on the organisation to determine their risks and implement appropriate technical and organisational controls to attempt mitigation. Furthermore, there is currently no GDPR compliant framework, even though several GDPR-friendly standards do exist (Cyber Essentials/IASME and ISO 27001).
What is Cyber Essentials?
The Cyber Essentials standard was originally born from a joint UK Government and University project to identify why an increasing number of organisations were being impacted by internet-based attacks. From the study, five common weaknesses were identified:
- Boundary firewalls and internet gateway – ensuring your router/firewall is configured correctly and protects your organisation
- Secure configuration – disabling guest accounts, remove unused applications
- Patches and updates – in particular, operating system and 3rd party software updates
- Access control – ensuring organisations have policies in place for user and administrative account management
- Malware protection – best practice AV configuration
The UK’s National Cyber Security Centre awards Cyber Essentials licenses to Accreditation bodies in the UK. In turn, these have Certification Bodies who actually work with organisations to help them implement and formally meet the standard. Each accreditation body takes a slightly different implementation approach.
There are two variants available: a self-assessed version with a standard fee of £300 (Q&A assessment), and an audited version which typically starts at £1500 (IASME stipulates a two-stage process consisting of Q&A assessment and an onsite sample audit by a certified moderator). At CyberSecuritiesUK, we have been working with organisations over the past several years, and most feel Cyber Essentials is an easy standard to meet. To some degree it is, however it does have a number of nuances that, if underestimated, may result in failure.
GDPR and Cyber Essentials – what’s the connection between them?
Cyber Essentials helps you start to meet the data protection requirements of GDPR. It doesn’t, however, touch on the Privacy area at all. Since GDPR stipulates that you must be able to demonstrate ongoing compliance, what better way than meeting an already existing Cyber Standard as part of a wider information framework programme?
Cyber Essentials also helps you to start your journey in relation to GDPR Article 32 which requires Data Controllers and Data Processors to “implement technical and organisational measures that ensure a level of data security appropriate for the level of risk presented by processing personal data.”
Don’t forget: the GDPR also requires that any third-party organisations (Data Processor/Joint Data Controllers) that share your data must also implement appropriate standards. An easy way of identifying organisations that have taken data protection seriously would be to ask if they have met Cyber Essentials standards.
The GDPR encompasses a wide number of requirements, ranging from policies/procedures to technical controls. Cyber Essentials’ primary focus is that of basic technical controls and, once achieved, will help you start your journey.
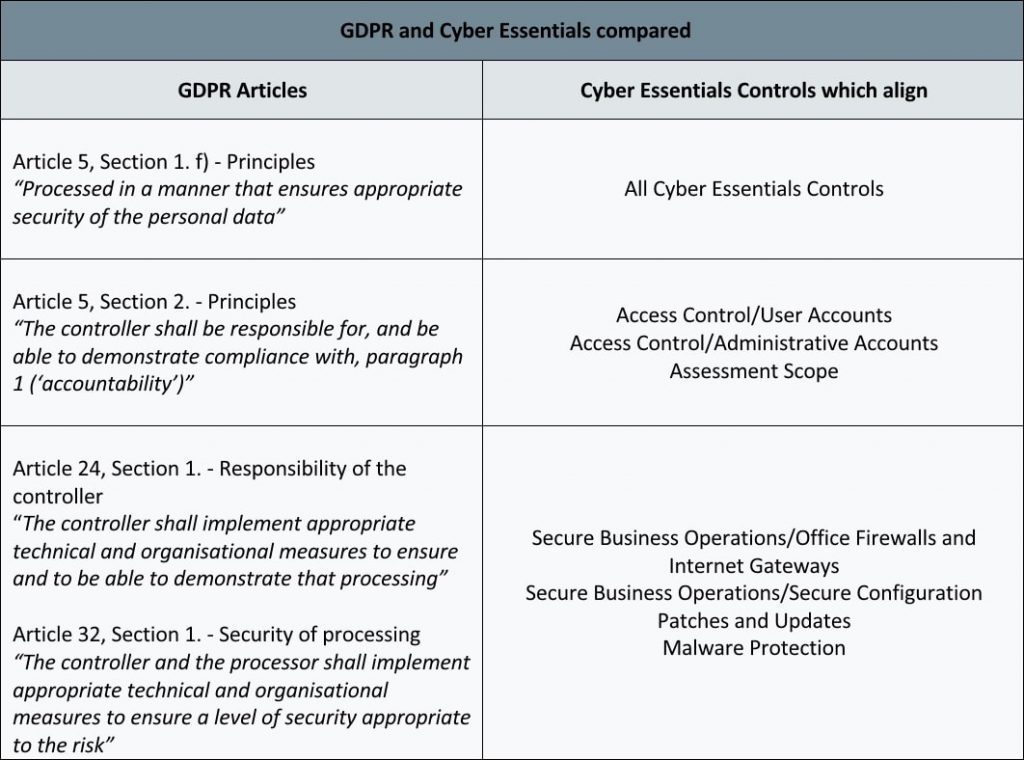
Refer to the following table for an overview of the GDPR Articles that are aligned with Cyber Essentials:
Cyber Essentials as a cost effective first step
So, what are the benefits of certification against Cyber Essentials in the context of the GDPR? While Cyber Essentials on its own won’t make you GDPR ready, it’s a cost-effective first step. Every organisation should seriously consider it as part of a wider programme.